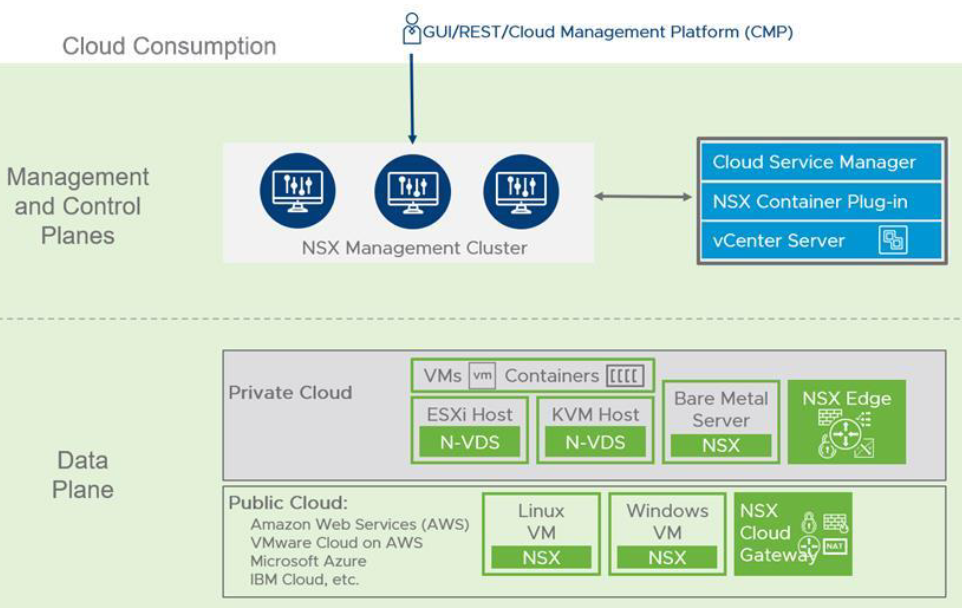
One of the new features which has been added to NSX-T 3.0 is supporting RBAC with Native Active Directory. In previous version of NSX-T we had to use VMware Identity Manager (vIDM) to be able to add users and groups from Active Directory for RBAC purposes. In set posts I have already described how to install and configure vIDM with NSX-T. I still believe configuring RBAC through vIDM has some added value like Multi-Factor Authentication(MFA).
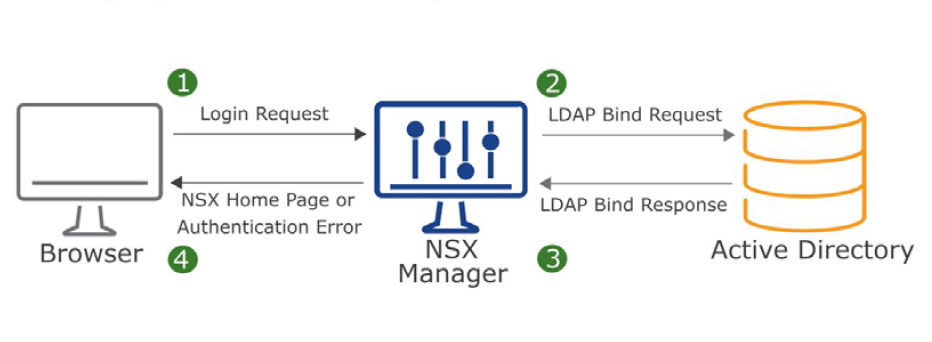
To setup NSX-T Role-based Access Control(RBAC) it’s better to create groups in Active Directory and add users into the group for two reasons. First it’s easier to add a group with couple of users as members rather than assign role to many users in NSX-T. Second, with help of Group Policy you can define a “Restricted Group” and it locks down membership to that group. As a result it provides a layer of security.
Continue reading “Configure NSX-T 3.0 RBAC with Native Active Directory Integration”