When it comes to connecting an on-premises VMware environment to Azure VMware Solution(AVS), ExpressRoute is the recommended & preferred connectivity method. But in some cases using a VPN tunnel is the only viable connectivity solution to AVS environment.
NSX-T Tier-0 or Tier-1 gateways could be used to connect on-premises VMware environment to AVS. On the Azure side, Virtual WAN(vWAN HUB) will be provide the transit connectivity through a ExpressRoute Gateway into AVS infrastructure. I am going to walk you through the configuration of both NSX-T Tier-1 GW and Azure Virtual WAN to have a complete setup.
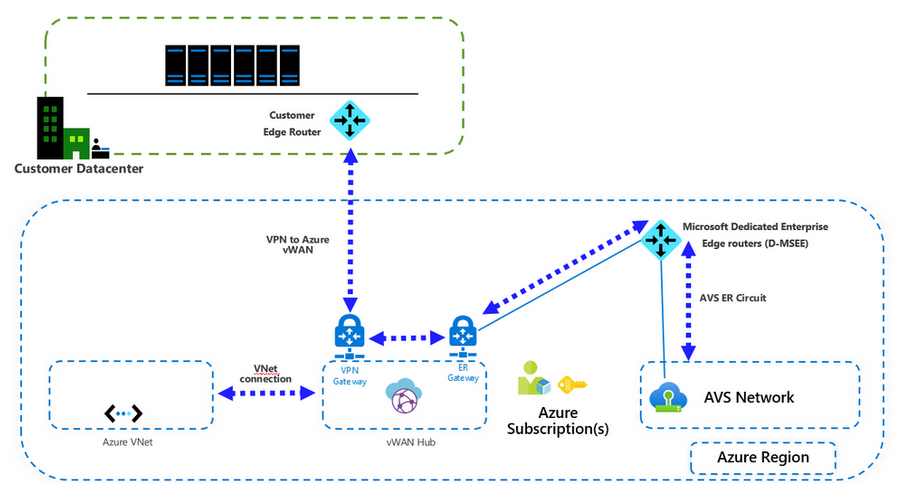
First we are going to bring up the VPN gateway on Azure side and then will jump into NSX-T to set up the Tier-1 Gateway. In Azure portal we should search and choose Virtual WAN to start the VPN gateway configuration.

In the Virtual WAN click on Add button and fill in the required information to create the new Vrtual WAN. Since are going to connect this vWAN to ExpressRoute gateway later, it is important to choose Standard for vWAN type.
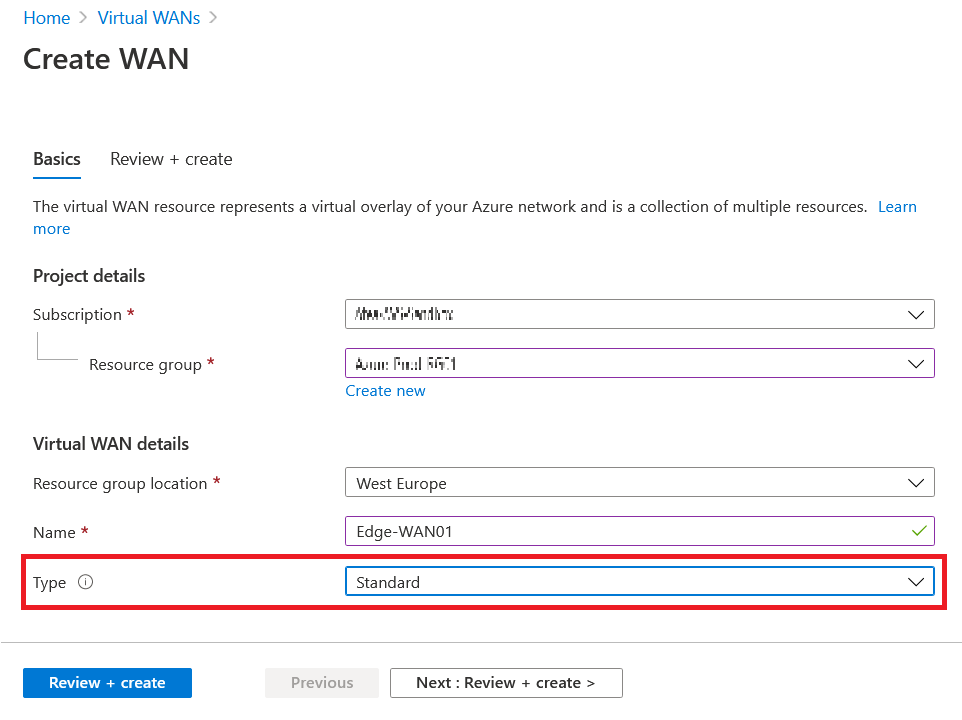
When the vWAN deployment is done you would see the following screen. Click on Go to resource to continue the VPN implementation.
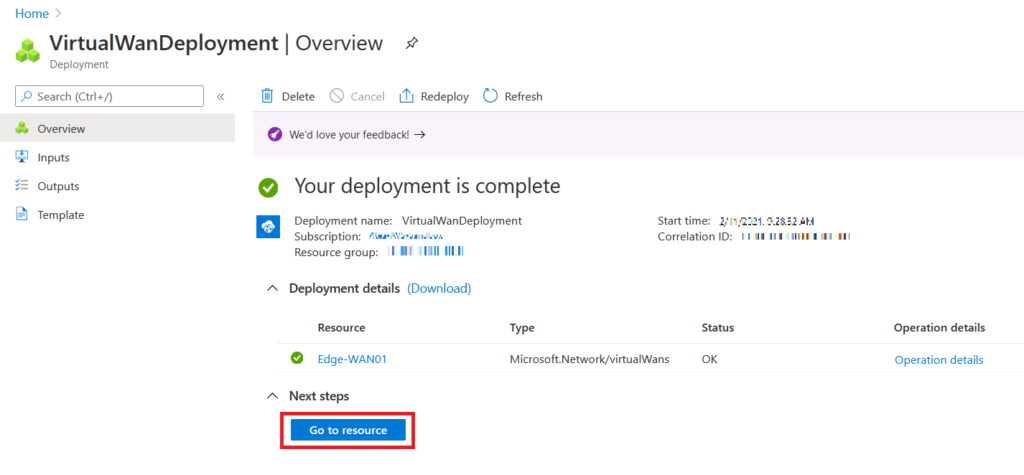
We should now create a Hub inside the vWAN and this would be used as a central point for connectivity of vNets and other networking components. On the left panel under Connectivity choose Hubs and then click on Add button to start creating a Hub.
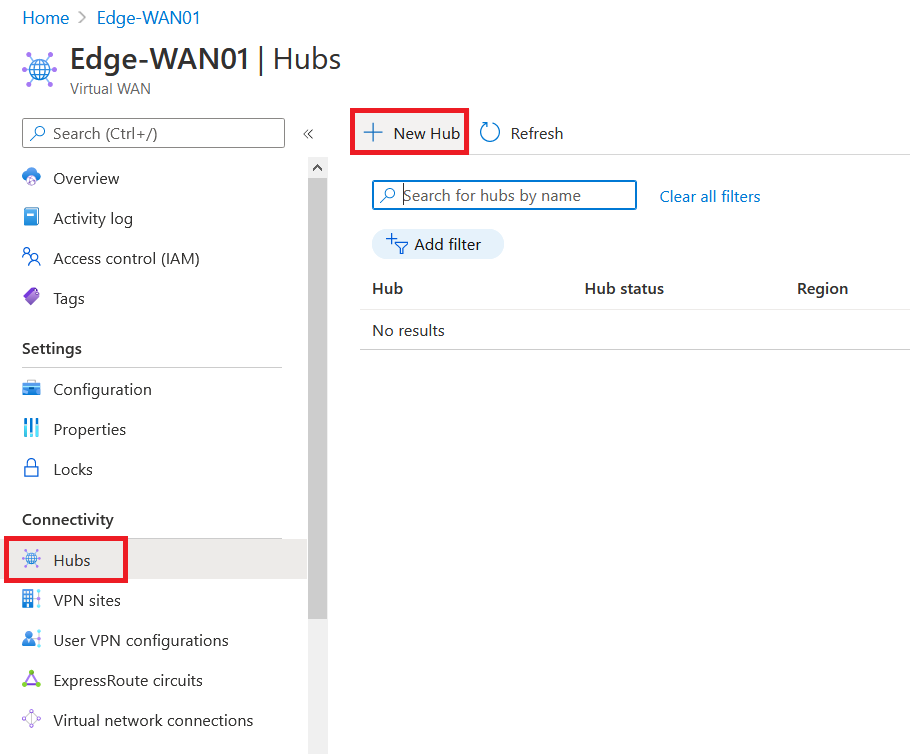
On the Basic page of the wizard choose a right Region(Same as AVS region), give it a Name and address space for Hubs components. This address space should not be overlapped with other address ranges that you are using.
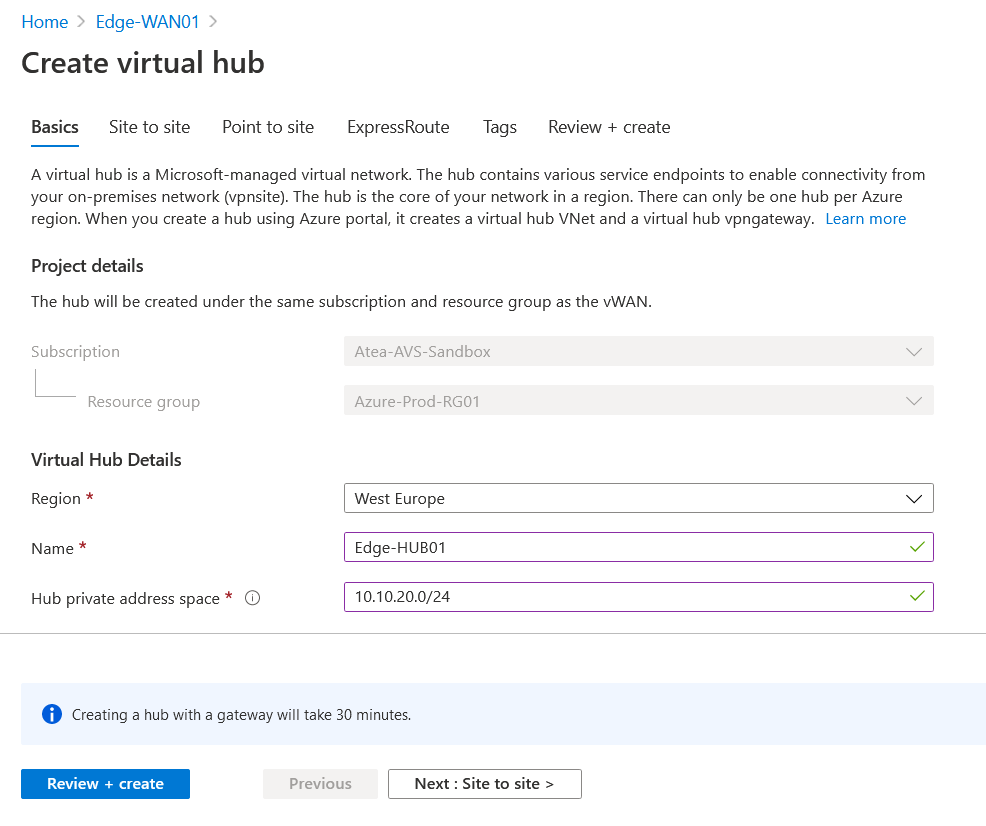
Since we are using this Hub for a site to site connectivity, make sure to enable Site to Site VPN Gateway. Based on you internet bandwidth and number of sites, choose a scale unit. Because I have one on-prem site with 300Mbps of bandwidth, I chose 1 scale unit which result on two gateways each with 500 Mbps of bandwidth.
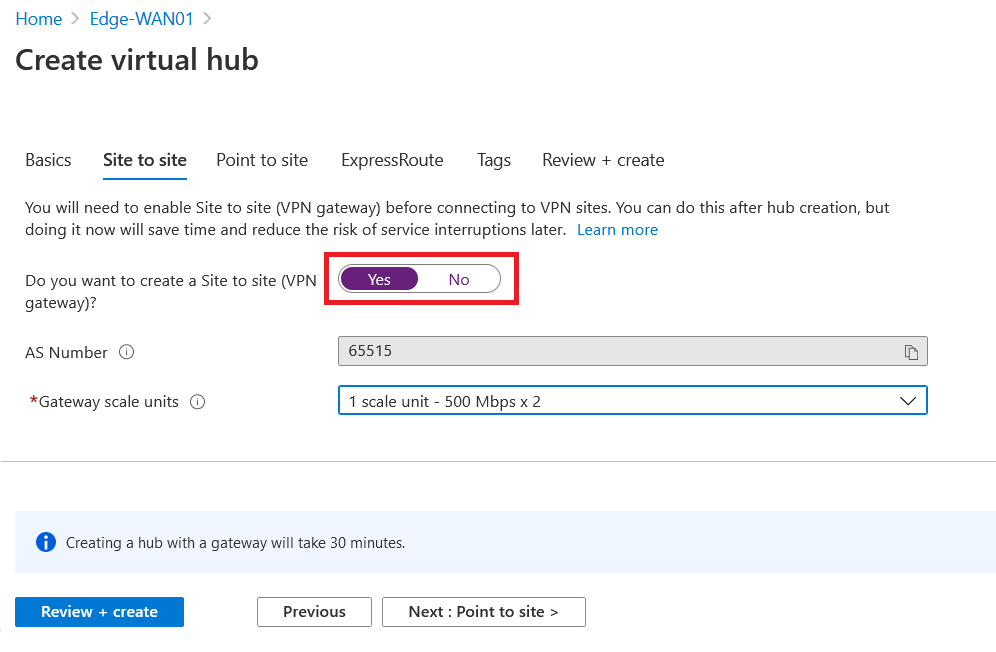
Since I am not planning to have end user connection terminated on this Hub, I disable Point to Site configuration. But as we discussed earlier, the AVS infrastructure will connect to this vWAN Hub with use of ExpressRoute (ER) and an ER Gateway, so I enable ER Gateway and configure 1 scale unit of 2 Gbps.
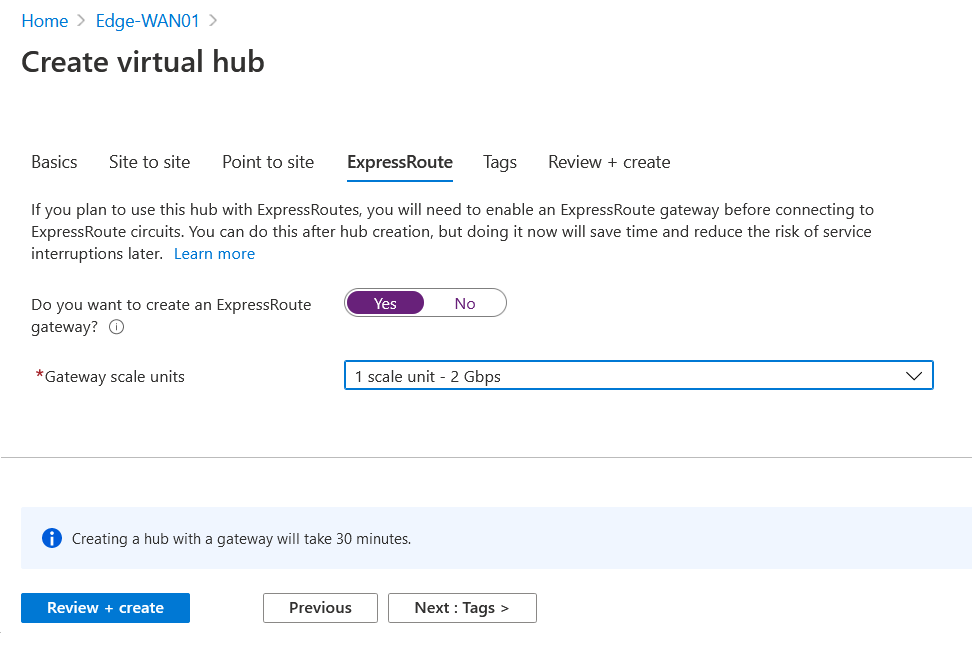
After this, configure possible Tags and then review and create the virtual HUB. Creating the virtual Hub will take a while and after it finishes please make sure you have Succeeded status both on Hub and Routing .
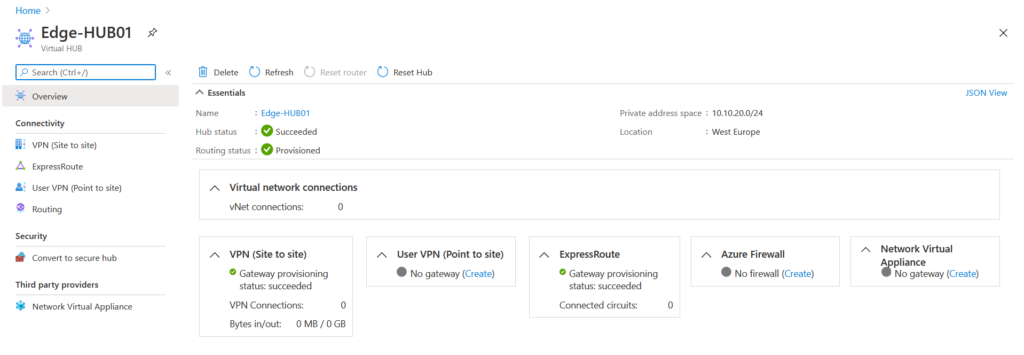
Next click on VPN (Site to Site) and by clicking on Gateway Configuration View/Configure you can find the public IP addresses of gateway that we will use on NSX-T as an endpoint address. To configure the VPN , click on Create new VPN site button.
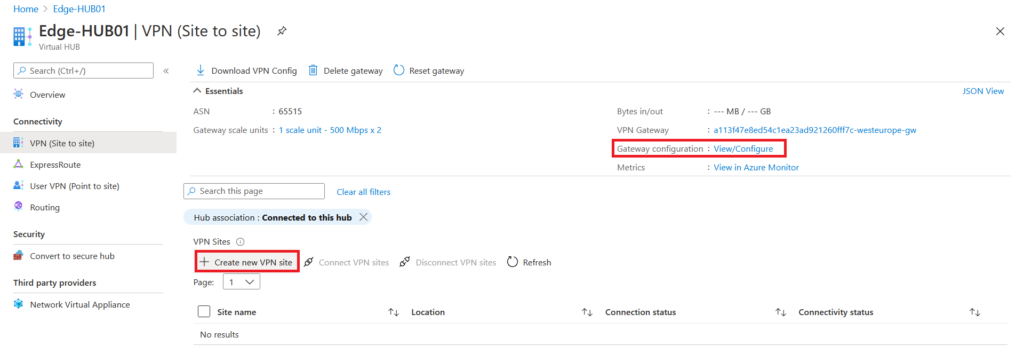
On the Create VPN site, choose the right Region, give it a name and optionally use a device vendor that is preferred like VMware or Cisco. It is also important to add the IP address range that you are using in the On-Prem side as the Private address space. We use 172.17.0.0/16 CIDR range On-Prem , so I add that range.
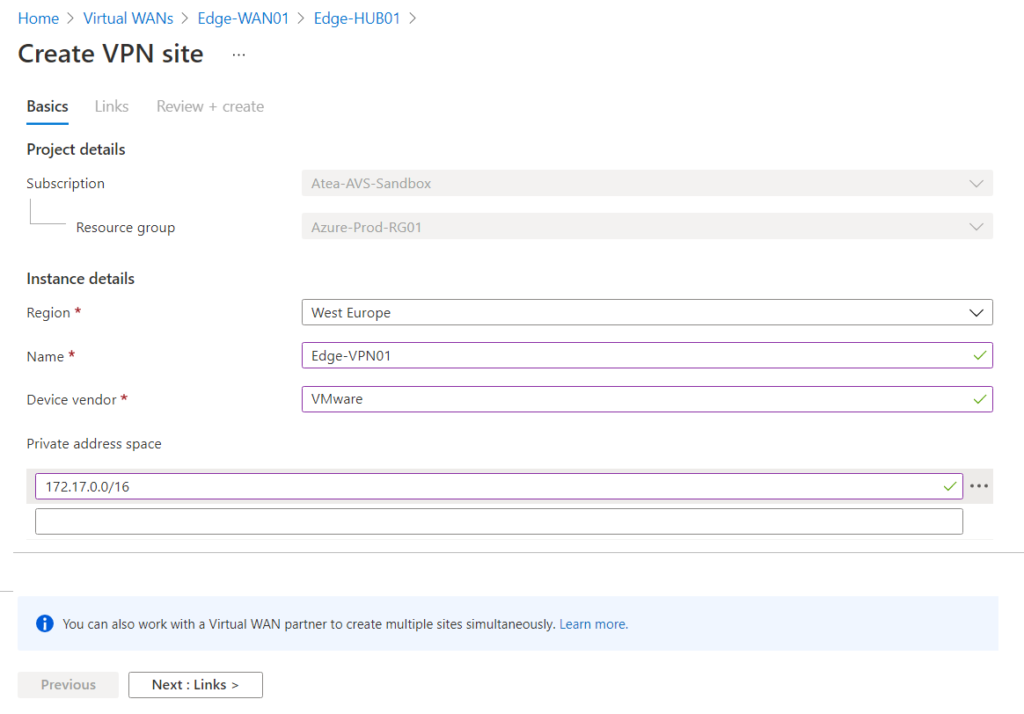
On the next page we should configure tunnel endpoint which reside On-Prem. Here is important to add your NSX-T public IP address in the Link IP Address box along side Link name, speed and provider name. If Route-Based VPN is being used instead of Policy-based, you can configure ASN of On-Prem BGP.
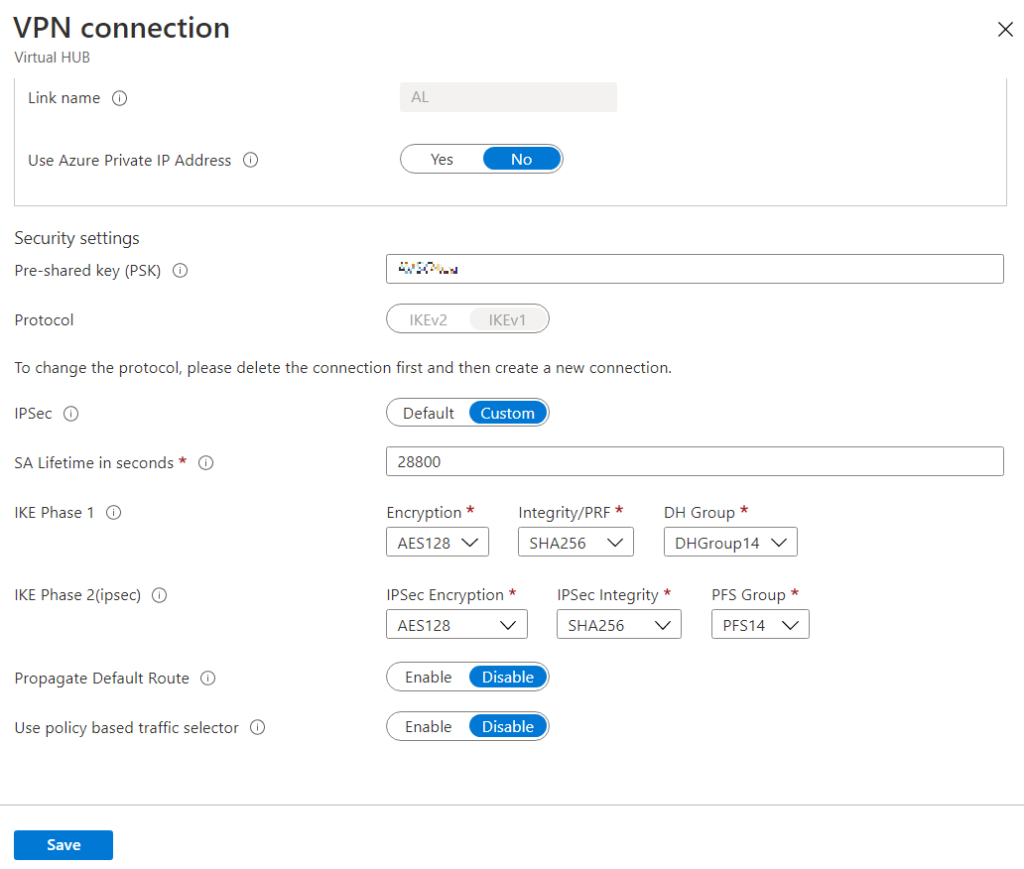
After VPN Site is created then we should Connect VPN site. In the connect wizard we should configure IPSec specific configuration.
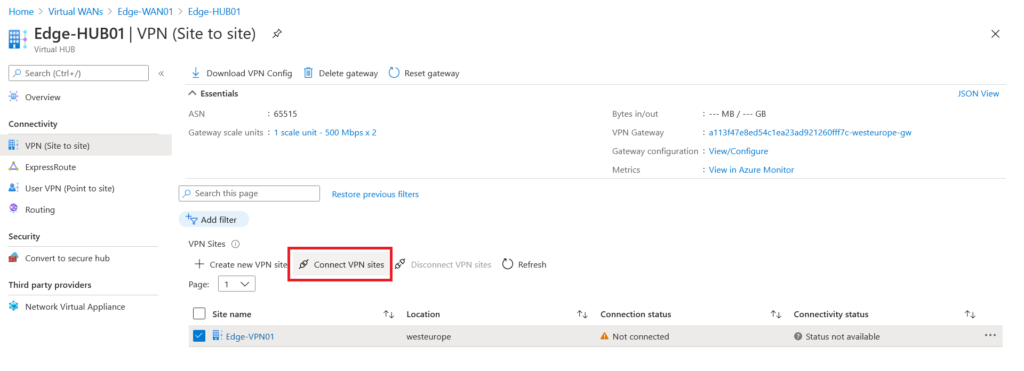
Here on this page Pre-shared key, IKE phase 1 and phase 2 could be configured. The following configuration used for this deployment but other configuration like IKE v2.
After configuring the VPN connection we are done with Azure side and should be proceed with On-Prem and NSX-T configuration. In the next blog post, we will continue with configuring NSX-T IPsec VPN implementation.